- Cisco Anyconnect Ssl Certificate
- Anyconnect Ssl Rekey Time
- What Is Cisco Anyconnect
- Anyconnect Ssl Vpn
- Anyconnect Ssl Vpn
In this post I am using an android mobile phone and downloaded anyconnect ICS+. Cisco ASA software version 9.1(4), ASDM version 7.1, with anyconnect essential license and anyconnect for mobile license. This demonstration will configure IPsec and SSL remote access VPN. STEP-2: Connect to your authorized Legacy Legacy EMC SSL VPN Gateway! Important: The Cisco Anyconnect gateway 'connect' field will be empty and you must obtain that from your Legacy EMC project owner and paste it or type it in. It will be in the form of 'tpa-vpn-xxxx-yyy.Legacy EMC.com' where 'xxxx' represents country and 'yyy' sub-region.
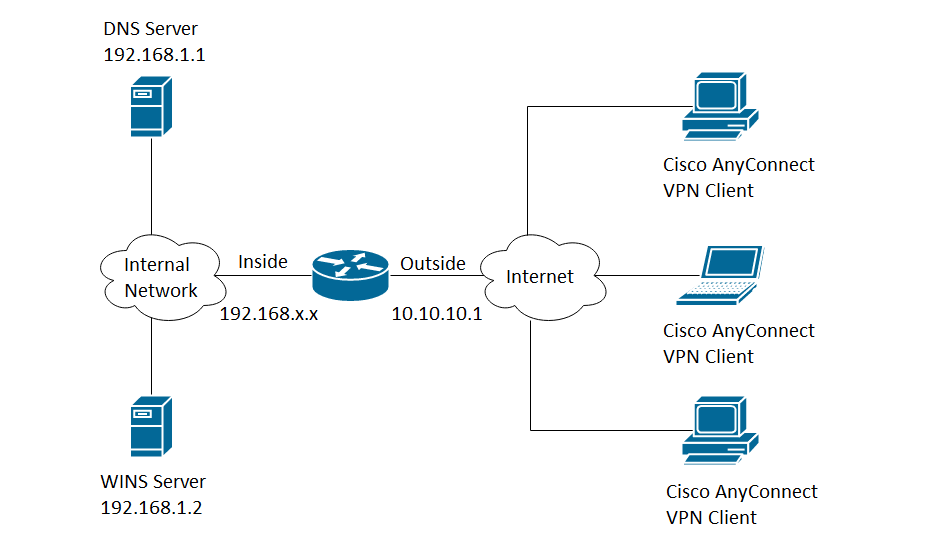
The Cisco SSL VPN is a downloadable remote access tool that allows users to access certain protected resources and services while they are away from campus.
The Cisco SSL VPN can be accessed either via an installed piece of software (“AnyConnect”) on your USC or personal computer, or via a web browser. A link to download the client to your computer, as well as a link to access the web VPN, are available in the right-hand toolbar of this page.
If prompted by the Cisco AnyConnect SSL VPN software for a URL to enter to connect to, type in sslvpn.usc.edu. Unless you have specific requirements or are accessing the USC network through the VPN from a location with special network requirements, you will likely want to select the Home or OffCampusOther connection profile. For more information on the different connection profile available and what each one does, visit this page on the USC Information Technology Services site.
The SSL VPN is also available for download as a free smartphone app. For iOS devices, click here or search for “Cisco AnyConnect” on the Apple App Store. For Android devices, click here or search for “AnyConnect” on Google Play.
The SSL VPN also has a feature known as Start Before Logon, which is enabled on Provost IT-configured computers. This feature allows users to login to their Provost accounts on their computers and access Provost IT-provided resources by initiating their connection at the Windows login screen, rather than through opening the application after logging in. For more information on this feature, contact us.
Additional Resources
- Frequently Asked Questions about the VPN, including a details on each connection profile
Eligibility
- Any USC staff, faculty, student, or iVIP
Data Security
- Approved to transmit high, medium, and low-risk data
Pricing
- Free for eligible users
Introduction
This document describes how to configure a Cisco AnyConnect Management tunnel on a Cisco Firepower Threat Defense (FTD) that is managed by Cisco Firepower Management Center (FMC). In example below Secure Sockets Layer (SSL) is used to create Virtual Private Network (VPN) between FTD and a Windows 10 client.
Contributed by Daniel Perez Vertti Vazquez, Cisco TAC Engineer.
Prerequisites
Requirements
Cisco recommends that you have knowledge of these topics:
- Cisco AnyConnect Profile Editor
- SSL AnyConnect configuration through FMC.
- Client Certificate authentication
Components Used
The information in this document is based on these software and hardware versions:
- Cisco FTD version 6.7.0 (Build 65)
- Cisco FMC version 6.7.0 (Build 65)
- Cisco AnyConnect 4.9.01095 installed on Windows 10 machine
The information in this document was created from the devices in a specific lab environment. All of the devices used in this document started with a cleared (default) configuration. If your network is live, ensure that you understand the potential impact of any command.
Background Information
From release 6.7, Cisco FTD supports configuration of AnyConnect Management tunnels. This fixes previously opened enhancement request CSCvs78215.
The AnyConnect Management feature allows to create a VPN tunnel immediately after the endpoint finishes its startup. There is no need that the users manually launch the AnyConnect app, as soon as their system is powered up, the AnyConnect VPN agent service detects the Management VPN feature and initiates an AnyConnect session using theHost Entry defined in the Server List of the AnyConnect Management VPN Profile.
Limitations
- Only Client Certificate authentication is supported.
- Only Machine Certificate Store is supported for Windows clients.
- Not supported on Cisco Firepower Device Manager (FDM) CSCvx90058.
- Not supported on Linux clients.
Configure
Configurations
Step 1. Create AnyConnect Management VPN Profile
Open the AnyConnect Profile Editor to create AnyConnect Management VPN Profile. The Management Profile contains all the settings used to establish the VPN tunnel after the endpoint boots up.
In this example a Server List entry that points to Fully Qualified Domain Name (FQDN) dperezve.jyoungta-labdomain.cisco.com is defined and SSL is selected as the primary protocol. To add a Server List navigate to Server List and select Add button, fill the required fields and save changes.
Besides to the Server List, the Management VPN Profile must contain some mandatory preferences:
- AutomaticCertSelection must be set to true.
- AutoReconnect must be set to true.
- AutoReconnectBehavior must be configured for ReconnectAfterResume.
- AutoUpdate must be set to false.
- BlockUntrustedServers must be set to true.
- CertificateStore must be configured for MachineStore.
- CertificateStoreOverride must be set to true.
- EnableAutomaticServerSelection must be set to false.
- EnableScripting must be set to false.
- RetainVPNOnLogoff must be set to true.
In AnyConnect Profile Editor navigate to Preferences (Part 1) and adjust settings as follows:
Then navigate to Preferences (Part 2) and uncheck the Disable Automatic Certificate Selection option.
Step 2. Create AnyConnect VPN Profile
Cisco Anyconnect Ssl Certificate
Addtional to the Management VPN Profile, the regular AnyConnect VPN Profile needs to be configured. The AnyConnect VPN Profile is used in the first connection try, during this session the Management VPN Profile is downloaded from FTD.
Use the AnyConnect Profile Editor to create the AnyConnect VPN Profile. In this case, both files contain the same settings so the same procedure can be follow.
Step 3. Upload AnyConnect Management VPN Profile and AnyConnect VPN Profile to FMC
Once the profiles are created, the next step is upload them to the FMC as AnyConnect File objects.
In order to upload the new AnyConnect Management VPN Profile to FMC navigate to Objects > Object Management and choose VPN option from the table of contents, then select the Add AnyConnect File button.
Provide a name for the file, choose AnyConnect Management VPN Profile as the file type and save the object.
Now, in order to upload the AnyConnect VPN Profile navigate again to Objects > Object Management and choose VPN option from the table of contents, then select the Add AnyConnect File button.
Provide a name for the file but this time choose AnyConnect VPN Profile as the file type and save the new object.
Profiles must be added to the object list and marked as AnyConnect Management VPN Profile and AnyConnect VPN Profile respectively.
Step 4. Create Group Policy
In order to create a new Group Policy navigate to Objects > Object Management and choose VPN option from the table of contents, then select Group Policy and clic on the Add Group Policy button.
Once the Add Group Policy window opens, assign a name, define an AnyConnect pool and open the AnyConnect tab. Navigate to Profile and select the object that represents the regular AnyConnect VPN Profile in the Client Profile drop down menu.
Then navigate to Management Profile tab and select the object that contains the Management VPN Profile in the Management Profile drop down menu.
Save the changes to add the new object to the existing Group Policies.
Step 5. Create New AnyConnect Configuration
The configuration of SSL AnyConnect in FMC is compound of 4 different steps. To configure AnyConnect navigate to Devices > VPN > Remote Access and select the Add button. This must open the Remote Access VPN Policy Wizard.
On Policy Assigment tab select the FTD device at hand, define a name for the Connection Profile and check the SSL checkbox.
On Connection Profile select Client Certificate Only as the authentication method. This is the only authentication supported for the feature.
Then select the Group Policy object created in step 3 in the Group Policy drop down.
On AnyConnect tab select the AnyConnect File Object according to the Operating System (OS) on the endpoint.
On Access & Certificate specify the certificate that must be used by the FTD to probe its identity to the Windows client.
Note: Since users shouldn't interact with AnyConnect app when using the Management VPN feature, the certificate needs to be fully trusted and mustn't print any Warning message.
Note: In order to prevent certificate validation errors, the Common Name (CN) field included in the Subject Name of the certificate must match the FQDN defined in the Server List of XML profiles (Step 1 and Step 2).
Finally, select Finish button on the Summary tab to add the new AnyConnect Configuration.
Step 6. Create URL Object
Navigate to Objects > Object Management and select URL from the table of contents. Then select Add Object in the Add URL drop down.
Provide a name for the object and define the URL using the same FQDN/User Group specified in the Management VPN Profile Server List (Step 2). In this example, URL must be dperezve.jyoungta-labdomain.cisco.com/AnyConnect_Management_Tunnel.
Save the changes to add the object to the object list.
Step 7. Define URL Alias
In order to enable the URL Alias in the AnyConnect configuration navigate to Devices > VPN > Remote Access and clic on the pencil icon to edit.
Then on the Connection Profile tab, select the configuration at hand, navigate to Aliases, clic on Add button and select the URL Object in the URL Alias drop down . Ensure the Enabled check box is selected.
Save changes and deploy configurations to FTD.
Anyconnect Ssl Rekey Time
Verify
After the deployment finishes, a first manual AnyConnect connection with the AnyConnect VPN Profile is needed. During this connection the Management VPN Profile is downloaded from FTD and stored in C:ProgramDataCiscoCisco AnyConnect Secure Mobility ClientProfileMgmtTun. From this point, subsequent connections must be initiated through the Management VPN profile without any user interaction.
What Is Cisco Anyconnect
Troubleshoot
For certificate validation errors:
- Ensure the root certificate for Certificate Authority (CA) is installed on the FTD.
- Ensure an identity certificate signed by the same CA is installed on Windows Machine Store.
- Ensure the CN field is included in the certificate and is the same as the FQDN defined in the Server List of the Management VPN Profile and FQDN defined in URL alias.
For Management tunnel not initiated:
- Ensure the Management VPN Profile has been downloaded and stored in C:ProgramDataCiscoCisco AnyConnect Secure Mobility ClientProfileMgmtTun.
Anyconnect Ssl Vpn
- Ensure the name for the Management VPN Profile is VpnMgmtTunProfile.xml.
Anyconnect Ssl Vpn
For connectivity problems collect DART bundle and contact Cisco TAC for further research.
